BlueHens CTF 2024
Hello there, i got to participate in the BlueHens 2024 CTF, organized by the Blue Hens academic team from the University of Delaware with the team pwnus you can get the whole ctf write up here
Training Problem Intro to Web
This is a simple web challenge that involved exploiting git version control.
We start off with visiting the site where we get this prompt.
This suggests that the developer was using version control to manage the site. From my knowledge this allows the dev to pop back to a stable version of the site in case the site crashes after a commit or making a change…
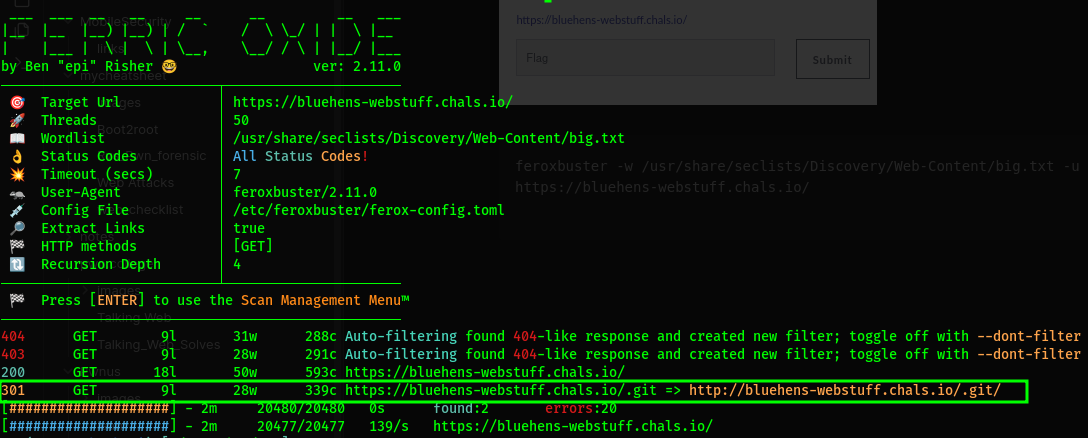
Checked the source code but got no luck so i opted to scan for other directories that may be of use.
1
2
feroxbuster -w /usr/share/seclists/Discovery/Web-Content/big.txt -u https://bluehens-webstuff.chals.io/
From the scan we get a .git directory, to get the contents of the directory we use git-dumper.
1
git-dumper https://bluehens-webstuff.chals.io/.git/ ./website
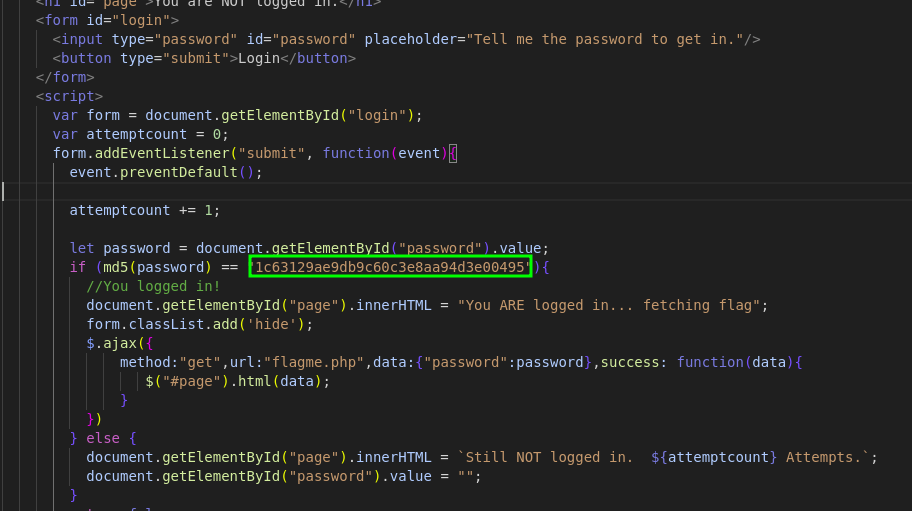
Analyzing the repository we find that the dev made two commits where the second one had a portion of the code removed. Here is the session of the code that was redacted for security measures :)
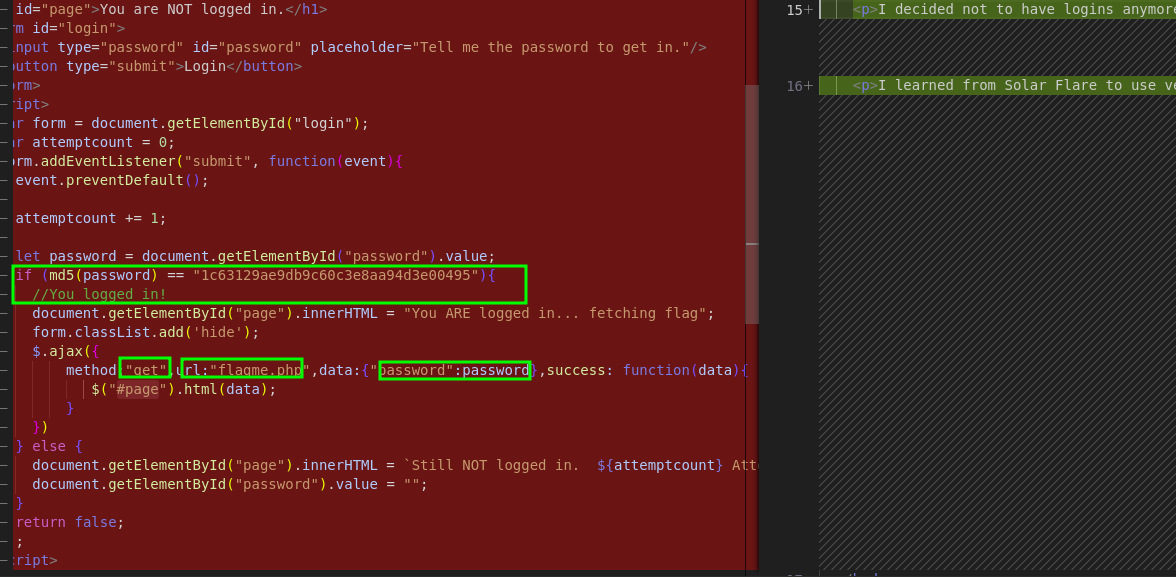
We grab the hashed password and u can use any online tool to decode the md5 hash to get:
1
1qaz2wsx
We set up git to enable version control for rollback.
To roll back to a previous version, identify the commit you want to revert to using:
1
2
3
4
5
6
7
8
9
10
11
12
13
git log
commit 6d11ca62644930fee1e2e48345c8d35bde2a95e7 (HEAD -> master)
Author: Andy Novocin <andy@fndrsng.com>
Date: Tue Oct 22 19:37:03 2024 +0000
no more passwords
commit 7f8c5ec67ec20a1ce111b64ec96cfefb472b1bb5
Author: Andy Novocin <andy@fndrsng.com>
Date: Tue Oct 22 19:35:53 2024 +0000
password based login?
reset your files to that point:
1
2
3
git reset --hard 7f8c5ec67ec20a1ce111b64ec96cfefb472b1bb5
HEAD is now at 7f8c5ec password based login?
Hosted the site locally on my machine and got this log in page.
Since i have the password i just authenticated.
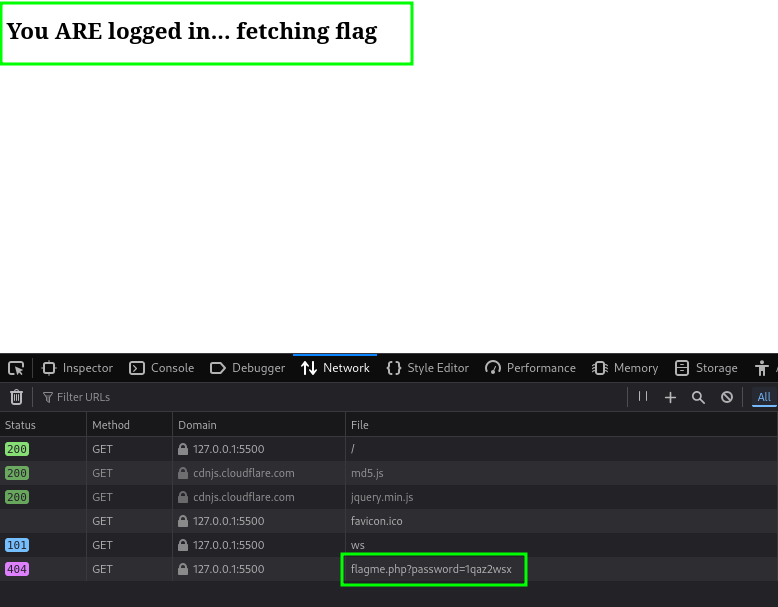
Analyzing the request we get that we are redirected to another page or file that has our flag. Capture the url query that authenticates using the password and queries the flag. We shall use it on the site hosted by the ctf.
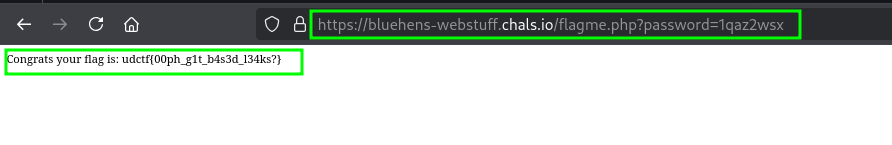
And there is our flag :)
1
udctf{00ph_g1t_b4s3d_l34ks?}
Inner Demons
Here is another simple forensic challenge where we are given an image to work our way around it.

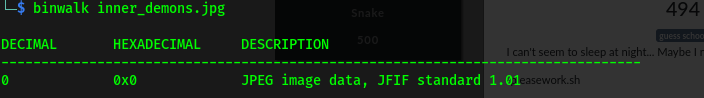
Upon downloading the challenge we start with checking what kind of a file it is.
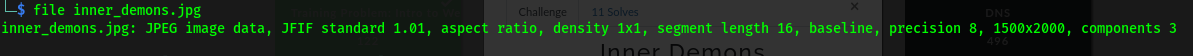
We use binwalk to check if the image has some embedded files.But no luck actually.
1
binwalk inner_demons.jpg
From here lets view the image may be the file is just lying there :) Here is a quick way to view an image from the terminal.
1
eog inner_demons.jpg
Damn what are this??? Demons hahaha!!

Though binwalk gave us nothing i opted to brute force any file/data in the image. For this i will use stegseek since i have no idea of the kind of world list to use.
1
stegseek inner_demons.jpg
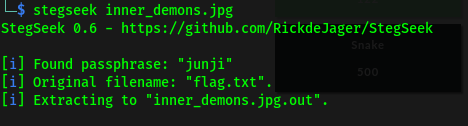
Got the passphrase and an output file that contains the flag :)
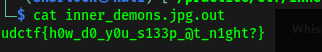
That was simple . Adios guys till the next ctf’s .